Introduction
Smallnet Information Services (SIS) is a server software suite that plays a similar role to Microsoft’s Internet Information Services (IIS), but for protocols in the small internet ecosystem. SIS provides integrated server support for Gemini, Gopher, Nex/NPS, Spartan, Misfin, Scroll, and Titan protocols. Using the built-in SIS Manager interface (accessed via Gemini), administrators can configure and manage multiple virtual servers across different protocols, defining their hostnames, certificates, and protocol-specific settings from a single administrative console.
Request Multiplexing
Incoming connections are multiplexed to each server based on the request’s protocol, SNI and ALPN information, and any information provided within the protocol’s request syntax. Multiplexing allows dynamic server configuration to take effect immediately without server restarts.
SIS uses port listeners to route incoming requests to the appropriate server. This allows for virtual hosting and multiple protocols on one port. However, some protocols have specific restrictions:
- Nex and Gopher don’t support virtual hosting, so they need dedicated ports
- Misfin servers on shared ports must use unique hostnames and their own root CA certificates
Since most protocols either use different ports or support virtual hosting, the above restrictions are easily avoided.
Security
SIS implements features that ensure the security of your system:
- All servers by default rate-limit incoming connections based on IP addresses.
- There is a global max concurrent connection limit.
- File permissions are taken into account when serving directories, files, and CGI scripts.
Permissions Under Unix Systems (unimplemented)
SIS will only serve world-readable content; all files and directories must be world-readable. If they are not, they are not served and are hidden from directory listings.
CGI scripts must be world-executable and world-readable to function properly.
Windows Systems (unimplemented)
Like Apache, when SIS is installed as a Windows service, it is ran under a particular user account created for the server. SIS will only serve content readable by this user. CGI scripts must also be executable by this user.
Client Library
SIS can be used as a Golang library to: extend an existing server, build a custom server from scratch, create CGI applications, or implement SCGI application servers. See the section on Using SIS as a Library for more information.
Installing
SIS is not in any software repositories at the moment.
Build instructions are provided for Unix and Windows for those who would like to build the program for themselves.
Building on BSD, Linux, and MacOS
Ensure that you have Golang 1.23.0 or above installed.
To build, clone the repo and run go build ./sis/.
git clone https://gitlab.com/sis-suite/smallnetinformationservices
cd smallnetinformationsystems
go build -o build/ ./sis/
You can then run SIS using the following command, providing it the root directory that all SIS configuration and server serve directories should be stored:
./build/sis start /path/to/SIS/directory
SIS will auto-generate a TLS certificate for the Gemini SIS Manager interface. By default, SIS Manager uses the address gemini://localhost:1995/.
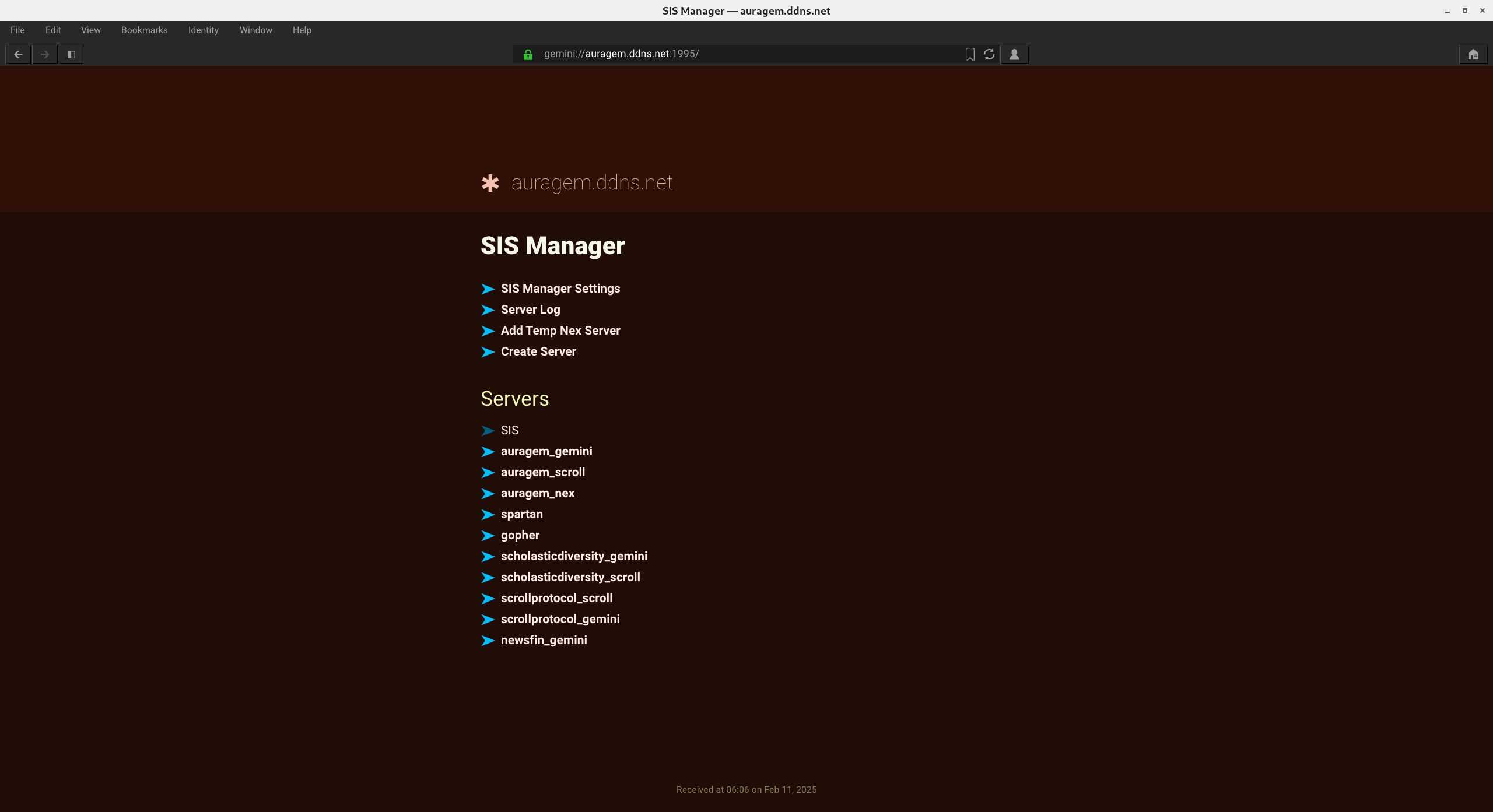
Using SIS Manager
SIS Manager is the admin dashboard interface from which you configure all of your servers. It allows you to:
- Create temporary or permanent servers
- Add, Remove, or Modify host configuration for each server
- Manage server-specific settings
- View server logs
- Add, Remove, or Modify routes and serve paths, including for CGI and SCGI applications
- Manage TLS certificates
- Restart, Shutdown, and Update SIS
- Place servers into maintenance mode
Misfin Server (Unimplemented)
Users can receive mail through multiple methods: a user on the host system, via the Geminimail interface (if enabled), or through the Gemini-Misfin Access Protocol (GMAP) using supported clients. GMAP offers two different mechanisms that intend to mimic IMAP and POP3, respectively. GMAP’s Fetch Address is provided to mimic POP3 and can be configured to delete on fetch or not. The Fetch Address can also be given a query of a start date (in ISO-8601 format) to fetch messages from. This can be used by clients to only get the latest messages that have not been fetched before.
The Misfin Server also allows you to create newsletters, mailinglists, and CGI Mailboxes. CGI Mailboxes are mailboxes that call out to a CGI script when a message has been received.
For users that use my misfinserver project, you can quickly transfer over to SIS by …
For users of the reference implementation, you can import by …
Finally, for users of Cipres’s fork of the reference implementation, you can transfer over to SIS by …
Misfin Geminimail Interface (Unimplemented)
You can set a misfin server to provide a geminimail interface for easy mail access to users. This is usually served over the same port as the misfin server. However, you can instead serve it over a route of one of your Gemini servers.
Transfer from Misfin-Server (Unimplemented)
Scroll Server
Scroll Protocol Classification Strings
You can put these classification strings in abstract files or at the start of scrolltext files using the following syntax:
udc-class: [string or class integer]
The following strings can be used:
- class 0: “knowledge”, “docs”, “documentation”, “data”, “general science”, “general knowledge”, “reference”, “computer science”, “news”, “software repository”, “software repo”, “computer technology”, “howto”, “tutorial”, “devlog”
- class 1: “philosophy”, “psychology”
- class 2: “religion”, “theology”, “scripture”
- class 3: “social science”, “social sciences”, “law”, “politics”, “gender studies”, “sociology”, “LGBTQ+”, “military”, “military affairs”, “education”
- class 5: “mathematics”, “math”, “maths”, “natural science”
- class 6: “applied science”, “applied sciences”, “technology”, “tech”, “medicine”, “health”, “engineering”, “business”, “accountancy”, “accounting”
- class 7: “art”, “arts”, “entertainment”, “music”, “gaming”, “gaming video”, “gaming videos”, “sport”, “sports”, “fictional movies”, “fictional movie”, “fictional animation”, “fictional animations”, “fictional anime”, “fictional animes”, “fashion”, “beauty”, “culinary art”, “culinary arts”, “recreation”, “fitness”, “drama”, “performance”, “performance art”, “performance arts”
- class 8: “linguistics”, “language”, “langauges”, “literature”, “literary criticism”, “biblical criticism”, “memoir”, “personal log”, “personal blog”, “book review”, “movie review”, “video review”, “music review”
- class 9: “history”, “geography”, “biography”, “autobiography”
- class 4: “unclassed”, “unclassed software”, “general software”, “general aggregator”, “general directory”, “general index”, “menu”
Gopher Server (WIP)
Transfer from Gophernicus (Unimplemented)
Upload Protocols
Titan
Titan can be enabled on a Gemini server and provides multiple functionalities: You can set up specific upload routes for services that you provide, and you can also set it to allow uploads of any static file on the site, which provides an easy mechanism for admins to update their static files via Titan.
CGI and SCGI applications can also utilize Titan.
Spartan
NPS
Proxying
HTTP Proxy (Unimplemented)
You can configure an HTTP proxy for any Gemini or Nex server you have configured by setting the http-proxy field to the port you want to serve it over.
Proxy Between Protocols (WIP)
You can proxy between any of the file-serving protocols (gemini, gopher, nex, and spartan). When a request is made to a proxy route, it will proxy the request to the desired server and convert the output to the expected output for the proxy server. For example, one could proxy all routes on a gemini server to gopher and the output will be converted to gophermaps if needed.
Reverse Proxying (Unimplemented)
SIS provides reverse proxy support through the use of SNI.
Tor Proxy (Unimplemented)
CGI and SCGI (WIP)
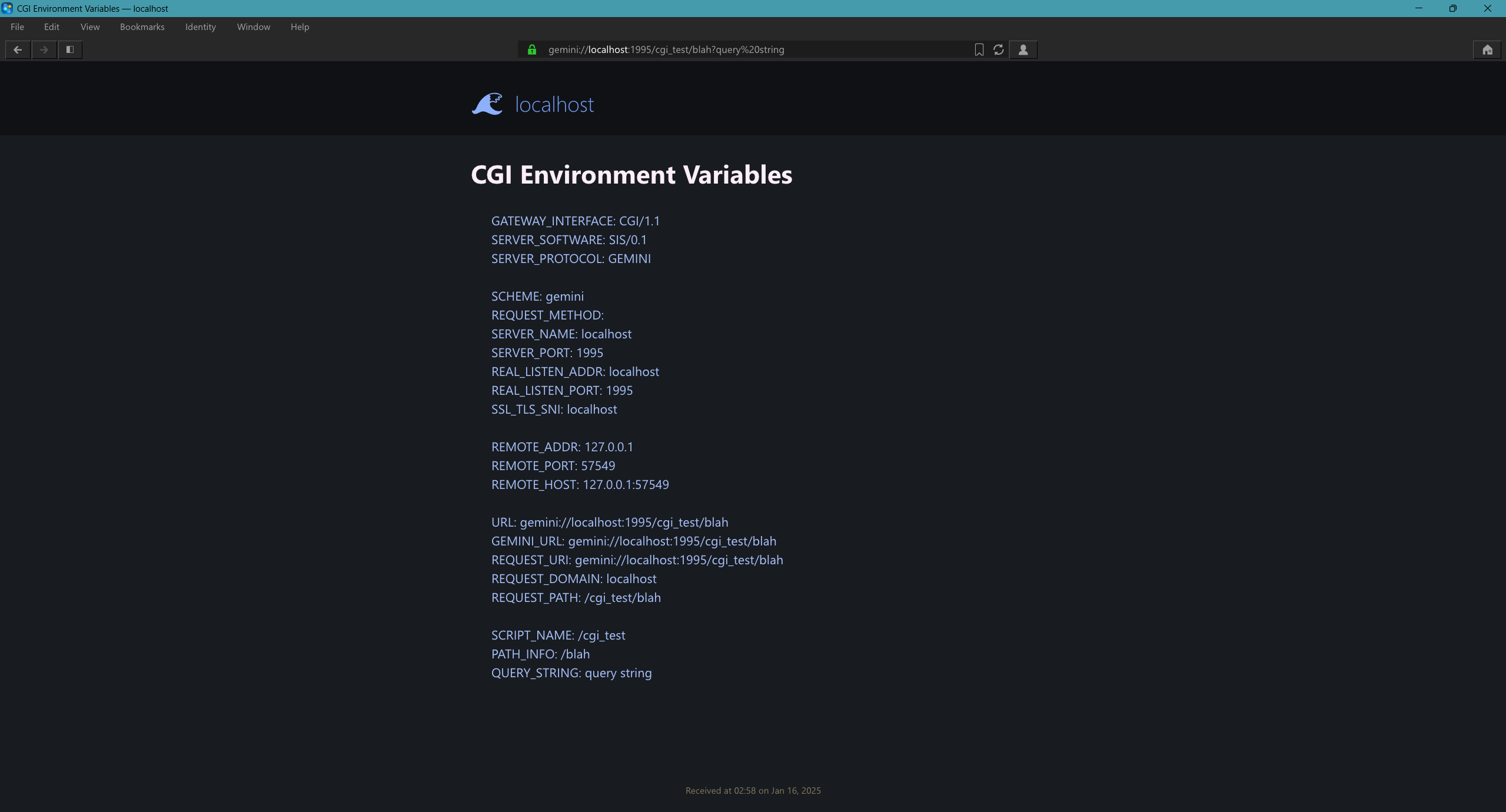
SIS supports CGI and SCGI for all protocols. The following variables are used:
Authorizers (Unimplemented)
An Authorizer script is a CGI script/SCGI server that is given TLS Client Certificate information, as well as path information, and hands back to the server (SIS) whether the user is authorized to access that resource. The server (SIS) then responds to the client with an error or, if authorized, the data that they requested, calling out to another CGI script/SCGI application server to access the resource data if necessary. This model is based off of FastCGI Authorizer scripts, but modified to work with CGI and SCGI. How each Authorizer should respond is detailed below.
Responses should use Gemini’s response format, regardless of protocol, with exception to HTTP(S) which may use FastCGI’s HTTP Authorizer responses.
20success should be used if authorized, telling the server to proceed with sending the resource to the client.60may be used if no certificate was given and one is required.61response code should be used for unauthorized certificates.62response code should be used for invalid certificates.
??When a directory is being served, SIS with automatically look for a .authorizer executable in a given directory and use it as an authorizer script for that directory’s contents.??
An authorizer script could handle authorization in three ways:
- comparing the client certificate hash to a list of known hashes
- check a database for the client certificate hash and its permissions
- call out to LDAP or some other authorization server
Internationalization
Except for Scroll Protocol, none of the other supported small internet protocols support specifying a language in a request. To get around this, one can set up routes specific to certain languages.
For responses, the server will try to detect the mimetype and language of the static document being sent back for the protocols that support these features. One can also manually specify these attributes in CGI/SCGI scripts and with the API.
TLS (WIP)
You can use the same or different TLS certificates for each server. If using one for multiple servers, make sure that the hostnames for each server is provided in the SAN field. Note that misfin servers always use their own separate server certificate because they act as Certificate Authorities to their respective mailbox certificates.
SNI and ALPN
SNI is used to support virtual hosting. When a client doesn’t use SNI, the server will default to the certificate of the first added server on a bind address + port listener, unless a misfin server is provided on the listener, then the misfin server’s certificate is used.
Most clients do not currently use ALPN (Application-Layer Protocol Negotiation) within the smallnet, but SIS does provide a list of protocols to allow for ALPN when available. ALPN will allow the TLS connection to quickly and explicitly negotiate the desired protocol for the incoming request. ALPN values sent over in the list include “gemini”, “titan”, and “misfin”.
Since SNI and ALPN are sent in the initial handshake, they are not encrpted. If a user is worried about SNI and ALPN being used to censor or block protocols on networks, then Tor and other censorship-resistant protocols are recommended. SIS provides support for Tor connections.
Using SIS as a Library
SIS can be used as a golang library to create custom server or SCGI application servers.
Configless Mode
When using SIS as a library, it can be initialized in configless mode, meaning it:
- Will not create an admin server
- Will not use a root SIS directory
- Will not store configuration files on disk
Configless mode is useful for servers that are dynamic-only or that handle static files themselves, or for creating an SCGI application server.
SCGI Application Server
package main
import sis "gitlab.com/sis-suite/smallnetinformationservices"
func main() {
// Start SCGI Application Server, in configless mode, meaning there will not be a SIS manager or configuration files.
context, err := sis.InitConfiglessMode()
if err != nil {
panic(err)
}
// For SCGI application servers, the Hostname is the expected hostname given from the main gemini server (aka. REQUEST_DOMAIN
// or SERVER_NAME), and the Port is the expected serve port given from the main gemini server (aka. SERVER_PORT).
hosts := [...]sis.HostConfig{
{BindAddress: "localhost", BindPort: "5001", Hostname: "localhost", Port: "1995", Upload: false, SCGI: true},
{BindAddress: "localhost", BindPort: "5001", Hostname: "localhost", Port: "1995", Upload: true, SCGI: true},
}
scgi_gemini_server := context.AddServer(sis.Server{Name: "AuraMuse", Type: sis.ServerType_Gemini}, hosts[:]...)
scgi_gemini_server.AddRoute("/", func(request sis.Request) {
request.Gemini("# SCGI Application Server Homepage\n")
request.Link("/test", "Test Link") // This makes sure the link is prepended with the SERVER_NAME, SERVER_PORT, and SCRIPT_NAME given to the SCGI application server.
request.Gemini("=> /test Another Test Link\n") // request.Gemini() also converts all links in the given gemtext to their correct version by prepending SCRIPT_NAME to absolute links.
})
scgi_gemini_server.AddRoute("/test", func(request sis.Request) {
request.Gemini("Hello World!\n")
})
context.Start()
}
Related Projects
Here are a list of related projects that can be used along with SIS:
Please note that most of these projects are unfinished.
Capsules using SIS
Here are a list of capsules that run off of SIS:
Planned Features
- Server maintenance mode
- Security: error out if a certificate’s permissions are too open, and don’t start that server if so
- UPnP to open ports for servers - must be manually enabled
- Finish NPS implementation (NPS Form)
- Misfin Server implementation: Misfin(B) and Misfin(C)
- Multi-user (pubnix) system setup
- Dynamic DNS setup
- SIS Manager User Management
- User permissions: access to specific servers, restrictions on host setup (mainly the bind_address and ports)
- Upload TLS certs
- Disk space quota
- Restrict CGI/SCGI
- Hosting registration: allow user registration for hosting.
- Dynamic DNS and Domain Name setup
- File Management
- File explorer over Gemini
- Titan upload (add new, delete, edit)
- Keep track of which version of page being updated: extend Titan and Gemini to use an identifier?
- Deployment - deploy static content to a server’s serve directory
- vcs projects
- Auto-start SCGI application servers that SIS will communicate with
- Use unix-domain sockets or pipes for SCGI application servers
- CGI/SCGI
- PATH_TRANSLATED
- Authorizers
- Non-parsed header scripts/application servers
- Internationalization
- Tor Onion Services
- Reverse Proxy
- Improved Gopher Protocol support
- Gophermap files
- Automatically add hostname and port to all lines that are missing them
- Include other gophermaps within a gophermap
- Need a way to link to files outside of server directory?
- Cache them?
- Gophermap files
- Streaming
- HTTP(S) Proxying
- Load Balancing
- Related Project Extensions
- Wiki System
- Code Management (Issue Tracker, etc.)
- Music and Radio Hosting
- Video Hosting
- FastCGI?
- Can handle multiple requests over one connection (internal multiplexing)
- Can also use multiple connections instead
- Gemini Proxying
- Since gemini allows you to put any URL in a request, you can use a gemini server as a proxy for other protocols (like http(s)).
- The multiplexer should be able to handle passing requests off to these proxy handlers.
- PSGI (Perl), JSGI (Javascript), Rack (Ruby), AJP, WSGI -> ASGI
- ?Support HTTP/HTTPS servers using another go library (or http package)?
Contributor Covenant Code of Conduct
Our Pledge
We as members, contributors, and leaders pledge to make participation in our community a harassment-free experience for everyone, regardless of age, body size, visible or invisible disability, ethnicity, sex characteristics, gender identity and expression, level of experience, education, socio-economic status, nationality, personal appearance, race, caste, color, religion, or sexual identity and orientation.
We pledge to act and interact in ways that contribute to an open, welcoming, diverse, inclusive, and healthy community.
Our Standards
Examples of behavior that contributes to a positive environment for our community include:
- Demonstrating empathy and kindness toward other people
- Being respectful of differing opinions, viewpoints, and experiences
- Giving and gracefully accepting constructive feedback
- Accepting responsibility and apologizing to those affected by our mistakes, and learning from the experience
- Focusing on what is best not just for us as individuals, but for the overall community
Examples of unacceptable behavior include:
- The use of sexualized language or imagery, and sexual attention or advances of any kind
- Trolling, insulting or derogatory comments, and personal or political attacks
- Public or private harassment
- Publishing others’ private information, such as a physical or email address, without their explicit permission
- Other conduct which could reasonably be considered inappropriate in a professional setting
Enforcement Responsibilities
Community leaders are responsible for clarifying and enforcing our standards of acceptable behavior and will take appropriate and fair corrective action in response to any behavior that they deem inappropriate, threatening, offensive, or harmful.
Community leaders have the right and responsibility to remove, edit, or reject comments, commits, code, wiki edits, issues, and other contributions that are not aligned to this Code of Conduct, and will communicate reasons for moderation decisions when appropriate.
Scope
This Code of Conduct applies within all community spaces, and also applies when an individual is officially representing the community in public spaces. Examples of representing our community include using an official email address, posting via an official social media account, or acting as an appointed representative at an online or offline event.
Enforcement
Instances of abusive, harassing, or otherwise unacceptable behavior may be reported to the community leaders responsible for enforcement at [christian.seibold32@outlook.com](emailto:christian.seibold32@outlook.com]. All complaints will be reviewed and investigated promptly and fairly.
All community leaders are obligated to respect the privacy and security of the reporter of any incident.
Enforcement Guidelines
Community leaders will follow these Community Impact Guidelines in determining the consequences for any action they deem in violation of this Code of Conduct:
1. Correction
Community Impact: Use of inappropriate language or other behavior deemed unprofessional or unwelcome in the community.
Consequence: A private, written warning from community leaders, providing clarity around the nature of the violation and an explanation of why the behavior was inappropriate. A public apology may be requested.
2. Warning
Community Impact: A violation through a single incident or series of actions.
Consequence: A warning with consequences for continued behavior. No interaction with the people involved, including unsolicited interaction with those enforcing the Code of Conduct, for a specified period of time. This includes avoiding interactions in community spaces as well as external channels like social media. Violating these terms may lead to a temporary or permanent ban.
3. Temporary Ban
Community Impact: A serious violation of community standards, including sustained inappropriate behavior.
Consequence: A temporary ban from any sort of interaction or public communication with the community for a specified period of time. No public or private interaction with the people involved, including unsolicited interaction with those enforcing the Code of Conduct, is allowed during this period. Violating these terms may lead to a permanent ban.
4. Permanent Ban
Community Impact: Demonstrating a pattern of violation of community standards, including sustained inappropriate behavior, harassment of an individual, or aggression toward or disparagement of classes of individuals.
Consequence: A permanent ban from any sort of public interaction within the community.
Attribution
This Code of Conduct is adapted from the Contributor Covenant, version 2.1, available at https://www.contributor-covenant.org/version/2/1/code_of_conduct.html.
Community Impact Guidelines were inspired by Mozilla’s code of conduct enforcement ladder.
For answers to common questions about this code of conduct, see the FAQ at https://www.contributor-covenant.org/faq. Translations are available at https://www.contributor-covenant.org/translations.
Contributing
License
BSD 3-Clause License
Copyright (c) 2024-2025, Christian Lee Seibold
Redistribution and use in source and binary forms, with or without
modification, are permitted provided that the following conditions are met:
1. Redistributions of source code must retain the above copyright notice, this
list of conditions and the following disclaimer.
2. Redistributions in binary form must reproduce the above copyright notice,
this list of conditions and the following disclaimer in the documentation
and/or other materials provided with the distribution.
3. Neither the name of the copyright holder nor the names of its
contributors may be used to endorse or promote products derived from
this software without specific prior written permission.
THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND CONTRIBUTORS "AS IS"
AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE
IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE
DISCLAIMED. IN NO EVENT SHALL THE COPYRIGHT HOLDER OR CONTRIBUTORS BE LIABLE
FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL
DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR
SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER
CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY,
OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE
OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.